Advertisement
Ethical Hacking Sliding Puzzle

- Play Again
- Preview:

Let me give some hints about its definition; it involves an authorized attempt to gain unauthorized access to a computer system, application, or data. Guess this puzzle and ace the challenge.

















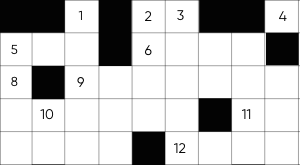
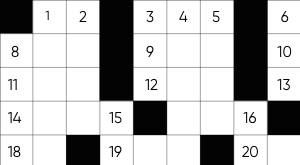
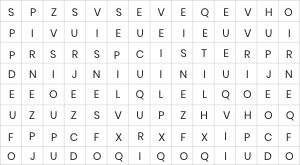
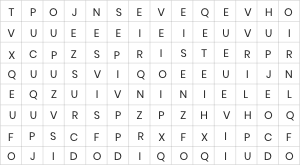

 Submitting your score, please wait...
Submitting your score, please wait...